
AWS EKS – Part 18 – Kubernetes Authentication with IAM Users
In this lesson, you will learn how to add additional IAM users to EKS clusters to allow your engineers to connect to Kubernetes clusters and do what they need based on their permissions. Authenticating to Kubernetes is one of the most important topics in Kubernetes Security. In AWS EKS, the only principal that can authenticate to the cluster is the cluster owner, “the user/role that deployed the cluster”, when the cluster is created. This is the default behaviour, and you should note the cluster owner user/role will not be saved in any configuration you can see, and you can’t change it after creating the cluster. Removing the cluster owner user/role will cause a permanent loose of cluster access, and to get access, you should remove and rebuild the cluster from scratch.
Best practice: To create clusters, use a specific user created for automation or an IAM role created for cluster creation, “to be assumed by users to create clusters”. Never allow individual accounts to create clusters because if they leave your company and you remove their user from the IAM service, you will lose the cluster owner.
Follow our social media:
https://www.linkedin.com/in/ssbostan
https://www.linkedin.com/company/kubedemy
https://www.youtube.com/@kubedemy
Register for the FREE EKS Tutorial:
If you want to access the course materials, register from the following link:
Register for the FREE AWS EKS Black Belt Course
AWS EKS Cluster Owner:
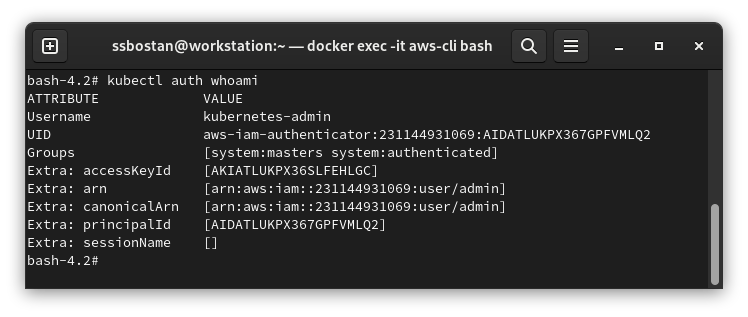
If you run kubectl auth whoami command with the cluster owner, you will get the following result. As you can see, this user is bound to system:masters Kubernetes group, which is a group with the highest privileges in the Kubernetes.
What is AWS IAM Authenticator?
AWS IAM Authenticator is a tool that allows IAM credentials to authenticate and access Kubernetes clusters. In AWS EKS, it runs as a part of the cluster control plane and is managed by AWS as part of their EKS service. You can also use it for non-EKS clusters and create a way to access non-EKS clusters using the AWS IAM service.
https://github.com/kubernetes-sigs/aws-iam-authenticator
IAM Authentication in AWS EKS Clusters:
In EKS clusters, all IAM principals are defined in aws-auth ConfigMap within kube-system namespace. This configuration is managed by both the EKS service and the cluster administrator. EKS edits this config to add/remove IAM Roles for worker nodes to allow them to join the cluster. The cluster admin can also edit this configuration to add/remove additional users/roles to the cluster. So, to add a new principal, we need to edit this resource. You can see a sample configuration here:
apiVersion: v1
kind: ConfigMap
metadata:
name: aws-auth
namespace: kube-system
data:
mapRoles: |
- rolearn: arn:aws:iam::231144931069:role/Kubedemy_EKS_Managed_Nodegroup_Role
username: system:node:{{EC2PrivateDNSName}}
groups:
- system:bootstrappers
- system:nodes
- rolearn: arn:aws:iam::231144931069:role/KubernetesAdmin
username: admin:{{SessionName}}
groups:
- system:masters
mapUsers: |
- userarn: arn:aws:iam::231144931069:user/kubedemy
username: kubedemy
groups:
- system:masters
mapAccounts: |
- "231144931069"
- "112233445566"mapRoles is a list of IAM roles authorized to access the cluster. For example, EC2 instances which want to join the cluster. You can also add a specific role for cluster administration and allow the role to be assumed by IAM users.
mapUsers is a list of IAM users authorized to access the cluster. Users are individuals like kubedemy user. They can login into the cluster and access the resources based on Kubernetes Roles attached to their username and groups.
mapAccounts is a list of AWS accounts authorized to access the cluster. As you can see, we don’t define usernames and groups for mapped accounts. IAM Authenticator automatically maps IAM ARN from these accounts to the username.
EKS Authentication with IAM User setup procedure:
- Create the IAM user in your AWS account.
- Attach EKS DescribeCluster permission to the user.
- Create Access and Secret keys for the user.
- Add IAM user configuration to the
aws-authconfigmap. - Configure AWS CLI for the new user.
- Update the Kubeconfig file and access the cluster.
Step 1 – Create a new IAM user:
We must create a new IAM user in our AWS IAM service. To create a user:
aws iam create-user \
--user-name kubedemy \
--tags Key=owner,Value=kubedemyStep 2 – Attach EKS policy to IAM user:
You must attach eks:DescribeCluster permission to the user if you want to use the aws eks update-kubeconfig command to generate the kubeconfig file. If you’re going to use the aws eks get-token command, you can ignore this step.
Create the policy document:
cat <<EOF > describe-kubedemy-cluster.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": "arn:aws:eks:eu-west-2:231144931069:cluster/kubedemy",
"Action": "eks:DescribeCluster"
}
]
}
EOFAttach the policy as an inline policy to the user:
aws iam put-user-policy \
--user-name kubedemy \
--policy-name Describe_Kubedemy_Cluster \
--policy-document file://describe-kubedemy-cluster.jsonStep 3 – Create IAM Access Key for the IAM user:
To create a new Access key for the user, run the following command:
aws iam create-access-key \
--user-name kubedemy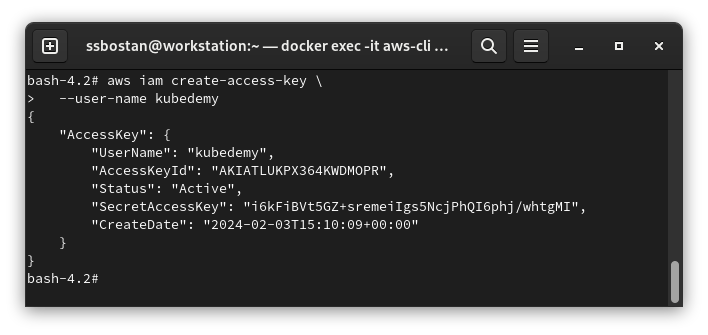
Step 4 – Add IAM User to EKS Cluster:
To add an IAM user to access the EKS cluster, you must add the user ARN in aws-auth ConfigMap within kube-system namespace. If you don’t have any worker nodes within the cluster, you must create this configmap. If you have any worker nodes, remember to keep their configuration within this configmap. If you accidentally remove any config related to the worker nodes, you will lose those worker nodes, as EKS uses this authentication method to allow worker nodes to join the cluster.
cat <<EOF > aws-auth.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: aws-auth
namespace: kube-system
data:
# Remember to keep worker nodes configurations.
# mapRoles: |
# ...
mapUsers: |
- userarn: arn:aws:iam::231144931069:user/kubedemy
username: kubedemy
groups:
- system:masters
EOFTo apply it to the cluster, run the following command:
kubectl apply -f aws-auth.yamlStep 5 – Setup AWS CLI to access the EKS cluster:
You must configure AWS CLI to be able to get a token or generate the kubeconfig file.
aws configure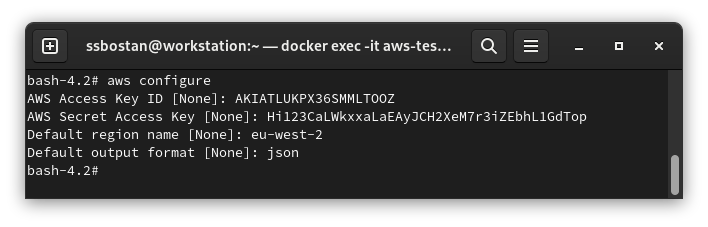
Step 6 – Create Kubeconfig and Access the cluster:
Now, it’s time to generate the kubeconfig and access the cluster. The new IAM user will get the username and groups we assigned to it in aws-auth configmap.
aws eks update-kubeconfig --name kubedemy
kubectl auth whoami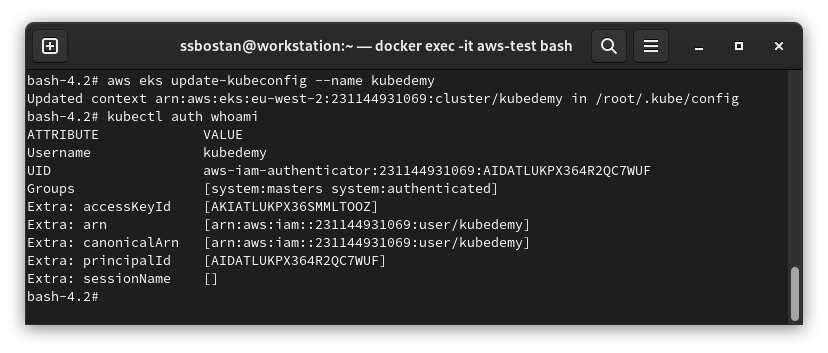
Results:
Here are the results of the previous commands; we need them in the next articles:
| IAM Username | kubedemy |
| IAM User ARN | arn:aws:iam::231144931069:user/kubedemy |
| IAM User Permissions | Allow=eks:DescribeCluster |
| ConfigMap Name | aws-auth |
| ConfigMap Namespace | kube-system |
| Username in Cluster | kubedemy |
| Groups in Cluster | system:masters |
Important tips:
- Never Delete the cluster owner user/role in your AWS account.
- Instead of using IAM users to create clusters, use IAM roles.
- Use IAM user authentication as a breakglass method or for automation.
- When changing
aws-auth, remember to keep the worker nodes’ configuration. - To allow users to access EKS clusters, use Roles or setup OIDC.
Conclusion:
In this lesson, you’ve learned how to setup EKS authentication using AWS IAM Authenticator with IAM users. This method should be used as a breakglass method for authenticating to the cluster or for automation purposes. If you want to allow users to access clusters, use IAM roles or OIDC, which will be explained in future articles.
If you like this series of articles, please share them and write your thoughts as comments here. Your feedback encourages me to complete this massively planned program. Just share them and provide feedback. I’ll make you an AWS EKS black belt.
Follow my LinkedIn https://www.linkedin.com/in/ssbostan
Follow Kubedemy LinkedIn https://www.linkedin.com/company/kubedemy
Follow Kubedemy Telegram https://telegram.me/kubedemy
