
AWS EKS – Part 36 – Backup and Restore EBS with Snapshots
Kubernetes provides a way to take and restore persistent volumes using Snapshots. The Kubernetes CSI project has defined the Volume Snapshot CRDs, and the external-snapshotter project implements functionality to watch for snapshot CRDs and trigger the snapshot endpoints within the CSI Driver. It’s important to know that the CSI Driver must support snapshots to allow the user and the snapshotter to take snapshots. The external-snapshotter project is a vendor-agnostic project that can be integrated with all CSI drivers implemented standard snapshot endpoints. The other solution implemented specifically for taking AWS EBS snapshots is the snapshot-controller project. In this lesson, we will work with this project to take EBS volume snapshots.
Follow our social media:
https://linkedin.com/in/ssbostan
https://linkedin.com/company/kubedemy
Register for the FREE EKS Tutorial:
If you want to access the course materials, register from the following link:
Register for the FREE AWS EKS Black Belt Course
What is Volume Snapshot?
Volume snapshots are point-in-time copies or backups of system data or state. In computing and storage, it refers to capturing the state of a data volume, database, or file system at a specific moment. Snapshots are commonly used for backup, recovery, and data protection purposes. In Kubernetes, volume snapshots capture the state of data from the Kubernetes PersistentVolume resources as the actual data is there.
How does snapshot work in EKS?
The EBS CSI Driver has implemented the volume snapshot capability, which is managed by the csi-snapshotter container within the driver controller. This container implements the required endpoints for managing volume snapshots and talking to AWS APIs to manage the actual EBS snapshots. On the other hand, the snapshot-controller project is responsible for managing the Snapshot CRDs and asking the EBS CSI Driver to create/delete volume snapshots for the requested volume.
EBS Snapshot setup procedure:
- Install the AWS Snapshot Controller.
- Create the CSI-based EBS StorageClass.
- Setup VolumeSnapshotClass for EBS volumes.
- Take EBS Volume Snapshots.
- Restore EBS Volume Snapshots.
Step 1 – Install the Kubernetes Snapshot Controller:
You can install the Snapshot Controller through the EKS Addons or install it using the Kubernetes CSI project through the Helm chart. The component doesn’t need any IAM policies as its job is to watch the Snapshot CRDs and call the CSI Driver. If you correctly install the EBS CSI Driver, it will work without issues or difficulties.
cat <<EOF > snapshot-controller.yaml
nodeSelector:
node.kubernetes.io/scope: system
tolerations:
- key: CriticalAddonsOnly
operator: Exists
EOF
aws eks create-addon \
--cluster-name kubedemy \
--addon-name snapshot-controller \
--configuration-values file://snapshot-controller.yaml \
--tags owner=kubedemyAfter installing the controller, you can find new CRDs created.
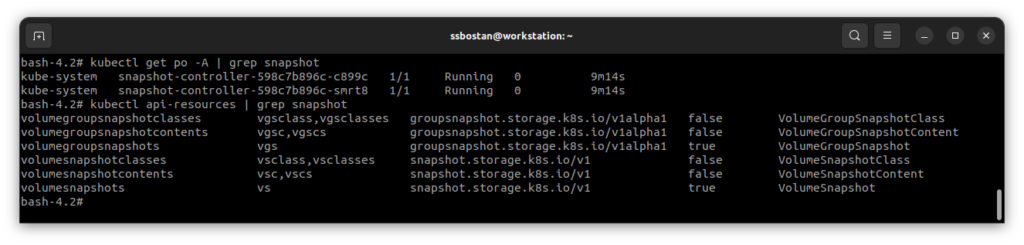
Step 2 – Create AWS EBS StorageClass:
Kubernetes doesn’t support snapshots for in-tree volume provisioners, which means the default gp2 StorageClass which uses kubernetes.io/aws-ebs provisioner within the cluster cannot be used when we need the volume snapshot feature. To fix the provisioner, you can edit the existing StorageClass or create a new one.
cat <<EOF | kubectl apply -f -
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: ebs
provisioner: ebs.csi.aws.com
volumeBindingMode: WaitForFirstConsumer
reclaimPolicy: Delete
EOFStep 3 – Create VolumeSnapshotClass in Kubernetes:
The VolumeSnapshot resource takes the class to help the controller trigger the right CSI driver to take the snapshot. To target EBS volumes, we must use the EBS CSI Driver.
cat <<EOF | kubectl apply -f -
apiVersion: snapshot.storage.k8s.io/v1
kind: VolumeSnapshotClass
metadata:
name: ebs
driver: ebs.csi.aws.com
deletionPolicy: Delete
EOFStep 4 – Take EBS Volume Snapshots:
Assume we have a running Pod using an existing PersistentVolumeClaim mounted into that Pod. To create a new snapshot, use the following manifest:
cat <<EOF | kubectl apply -f -
apiVersion: snapshot.storage.k8s.io/v1
kind: VolumeSnapshot
metadata:
name: test-ebs-snapshot-09082024
spec:
volumeSnapshotClassName: ebs
source:
persistentVolumeClaimName: test-ebs
EOFDepending on the storage size, it may take a while, around 1-2 minutes or more.
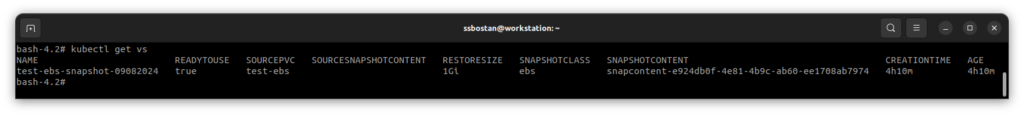
When it becomes available, the READYTOUSE flag becomes true.
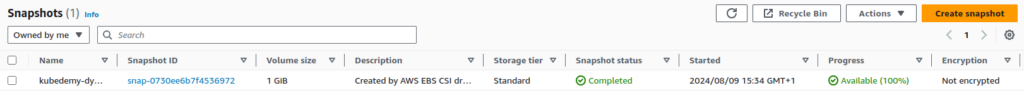
You must see the actual snapshot within your AWS account.
Step 5 – Restore EBS Volume from Snapshot:
We must create a new PersistentVolumeClaim to restore a snapshot and provide the VolumeSnapshot as its data source. To do so, run the following manifest:
cat <<EOF | kubectl apply -f -
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: test-ebs-restore
spec:
storageClassName: ebs
dataSource:
apiGroup: snapshot.storage.k8s.io
kind: VolumeSnapshot
name: test-ebs-snapshot-09082024
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
EOFThe above resource will create a new PVC pointing to the volume snapshot and wait for the first consumer to restore/create a volume from the snapshot.
cat <<EOF | kubectl apply -f -
apiVersion: v1
kind: Pod
metadata:
name: test-pod-restore
spec:
containers:
- name: alpine
image: alpine:latest
command: ["sleep", "infinity"]
volumeMounts:
- name: test-ebs-restore
mountPath: /data
volumes:
- name: test-ebs-restore
persistentVolumeClaim:
claimName: test-ebs-restore
EOFNow, your Pod will come up from the snapshot volume.
Conclusion:
Kubernetes Volume Snapshot can take backups from stateful applications’ storage and restore them if needed. EKS currently supports EBS snapshots, but this feature is unavailable for EFS or other storage. As explained in future articles, backup tools must be used instead to take backups from other storage. Remember that storage throughput and performance may be affected during the snapshot process.
If you like this series of articles, please share them and write your thoughts as comments here. Your feedback encourages me to complete this massively planned program. Just share them and provide feedback. I’ll make you an AWS EKS black belt.
Follow my LinkedIn https://linkedin.com/in/ssbostan
Follow Kubedemy’s LinkedIn https://linkedin.com/company/kubedemy
Follow Kubedemy’s Telegram https://telegram.me/kubedemy
