
AWS EKS – Part 6 – Deploy Bottlerocket Workers and Update Operator
Bottlerocket is a Linux operating system built by AWS to host containers, especially for Kubernetes. This OS has many pros and features compared to other available general-purpose operating systems. In this article, I explain why we use Bottlerocket OS for our EKS clusters and what we achieve if using Bottlerocket on EKS clusters.
Follow our social media:
https://www.linkedin.com/in/ssbostan
https://www.linkedin.com/company/kubedemy
https://www.youtube.com/@kubedemy
Register for the FREE EKS Tutorial:
If you want to access the course materials, register from the following link:
Register for the FREE AWS EKS Black Belt Course
Watch on YouTube:
Why Bottlerocket OS for Kubernetes:
- Bottlerocket is an open-source operating system built for containers.
- It is specially optimized for running containers on Kubernetes.
- Less overhead compared to general-purpose operating systems.
- Fewer tools, libraries, and binaries == fewer security issues.
- Support Kubernetes-based in-place upgrades using Kubernetes operators.
- Fully integrated with AWS EKS platform.
Bottlerocket deployment procedure:
- Deploy cluster worker nodes using managed node groups.
- Deploy Bottlerocket Update Operator to automate the update process.
- Investigate Bottlerocket Launch Template.
Step 1 – Deploy Bottlerocket worker nodes:
You can deploy Bottlerocket using all available deployment methods in EKS – fully managed node groups, node groups using custom launch templates and self-managed worker nodes. In this lab, we setup node groups using a fully managed method.
AWS EKS – Part 3 – Deploy Worker nodes using Managed Nodegroups
AWS EKS – Part 4 – Deploy Worker nodes using Custom Launch Templates
AWS EKS – Part 5 – Deploy Self-managed Worker nodes
Create cluster critical node group:
These worker nodes will be used to deploy cluster-critical applications like ingress controller, dashboard, monitoring, GitOps, CI/CD, security, etc. tools.
- Worker nodes label
node.kubernetes.io/scope=system - Worker nodes label
node.kubernetes.io/type=bottlerocket - These worker nodes are tainted with
CriticalAddonsOnlykey.
aws eks create-nodegroup \
--cluster-name kubedemy \
--nodegroup-name system-managed-bottlerocket-workers-001 \
--scaling-config minSize=2,maxSize=5,desiredSize=2 \
--subnets subnet-0ff015478090c2174 subnet-01b107cea804fdff1 subnet-09b7d720aca170608 \
--node-role arn:aws:iam::231144931069:role/Kubedemy_EKS_Managed_Nodegroup_Role \
--remote-access ec2SshKey=kubedemy \
--instance-types t3.medium \
--ami-type BOTTLEROCKET_x86_64 \
--capacity-type ON_DEMAND \
--update-config maxUnavailable=1 \
--taints "key=CriticalAddonsOnly,value=true,effect=NO_SCHEDULE" "key=CriticalAddonsOnly,value=true,effect=NO_EXECUTE" \
--labels node.kubernetes.io/scope=system,node.kubernetes.io/type=bottlerocket \
--tags owner=kubedemyCreate application node group:
These worker nodes will be used to deploy our workloads and applications.
- Worker nodes label
node.kubernetes.io/scope=application - Worker nodes label
node.kubernetes.io/type=bottlerocket
aws eks create-nodegroup \
--cluster-name kubedemy \
--nodegroup-name application-managed-bottlerocket-workers-001 \
--scaling-config minSize=2,maxSize=5,desiredSize=2 \
--subnets subnet-0ff015478090c2174 subnet-01b107cea804fdff1 subnet-09b7d720aca170608 \
--node-role arn:aws:iam::231144931069:role/Kubedemy_EKS_Managed_Nodegroup_Role \
--remote-access ec2SshKey=kubedemy \
--instance-types t3.medium \
--ami-type BOTTLEROCKET_x86_64 \
--capacity-type ON_DEMAND \
--update-config maxUnavailable=1 \
--labels node.kubernetes.io/scope=application,node.kubernetes.io/type=bottlerocket \
--tags owner=kubedemyStep 2 – Deploy Bottlerocket Update Operator:
This operator starts the Bottlerocket update controller as a Deployment and the update agent as a DaemonSet on all Bottlerocket nodes. Learn more from its repository.
Note: You need to install Helm before continuing this step.
Install cert-manager operator first:
helm repo add jetstack https://charts.jetstack.io
helm repo update
helm install cert-manager jetstack/cert-manager \
--namespace cert-manager \
--create-namespace \
--set "installCRDs=true"To install Bottlerocket Update Operator:
kubectl apply -f https://github.com/bottlerocket-os/bottlerocket-update-operator/releases/download/v1.3.0/bottlerocket-update-operator-v1.3.0.yamlNote: Find the latest version from their official repository.
Patch update operator DaemonSet to deploy the agent to system nodes:
kubectl -n brupop-bottlerocket-aws patch ds brupop-agent -p '{"spec":{"template":{"spec":{"tolerations":[{"operator":"Exists"}]}}}}'Add this label to Bottlerocket nodes:
kubectl label node $(kubectl get nodes -o jsonpath='{.items[*].metadata.name}' -l node.kubernetes.io/type=bottlerocket) bottlerocket.aws/updater-interface-version=2.0.0And check the Bottlerocket controller, apiserver and agents:
kubectl -n brupop-bottlerocket-aws get po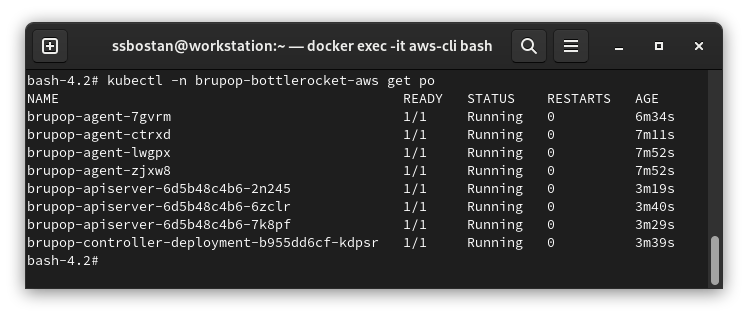
To check Bottlerocket updates, execute:
kubectl -n brupop-bottlerocket-aws get brs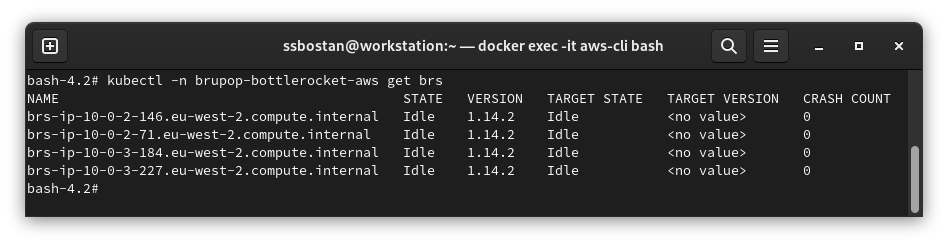
Step 3 – Investigate Bottlerocket Launch Template:
If you take a look at the EC2 Launch Template created for Bottlerocket worker nodes, you can see the User-data is entirely different from Amazon Linux one, and it’s because Bottlerocket use another syntax to initialize OS, and it’s wholly related to initiating Kubernetes kubelet component. Check the full settings here.
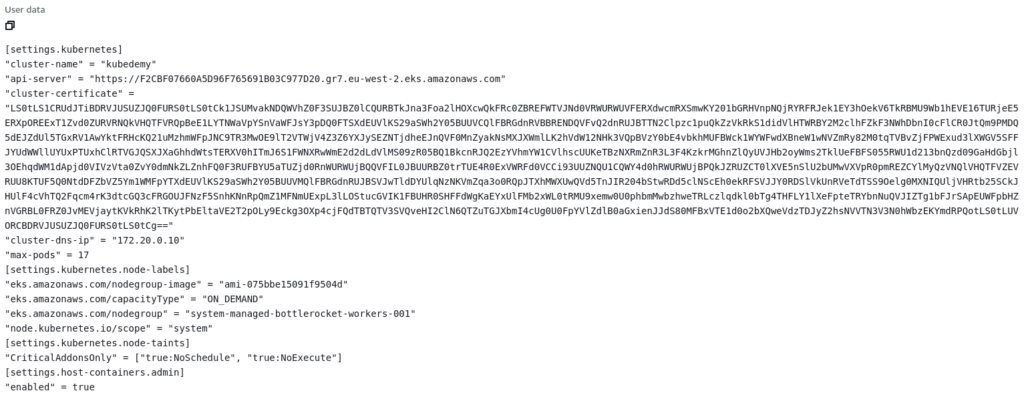
Conclusion:
Bottlerocket is a 3-year-old OS for containers, and it’s too early to say it’s ready for production environments. I had some challenges with the Bottlerocket Update Operator as well. The AWS team and other companies working on Bottlerocket have a long way to go to make it ready for production-grade environments.
If you like this series of articles, please share them and write your thoughts as comments here. Your feedback encourages me to complete this massively planned program. Just share them and provide feedback. I’ll make you an AWS EKS black belt.
Follow my LinkedIn https://www.linkedin.com/in/ssbostan
Follow Kubedemy LinkedIn https://www.linkedin.com/company/kubedemy
Follow Kubedemy Telegram https://telegram.me/kubedemy
